What You Need to Know About the Latest Changes to CIP-003-9 for Low-Impact Entities

NERC’s CIP-003-9 standard introduces new cybersecurity requirements for Low-Impact Bulk Electric System (BES) Cyber Systems, with a particular focus on managing vendor electronic remote access. Responsible Entities must now:
- Update their policies to include vendor remote access controls
- Be able to identify and disable vendor access
- Detect malicious communications tied to that access.
The changes aim to better manage third-party cyber risk even at low-impact sites.
We’ve provided a must-do checklist for low-impact entities to stay on track and simplify your path to compliance.
Cybersecurity requirements for Low-Impact Bulk Electric System (BES) Cyber Systems continue to evolve, and the latest update – CIP-003-9 – introduces new expectations for how Responsible Entities manage vendor electronic remote access. These updates are designed to reduce risk by strengthening detection, control, and response mechanisms for external vendor connections.
Here’s a quick breakdown of what’s changing and how you can prepare.
Key Updates in CIP-003-9 for Low-Impact Entities
Here’s a summary of the new CIP-003-9 requirements specifically targeting vendor electronic remote access for Low-Impact BES Cyber Systems:
- Cybersecurity policies must now include vendor remote access controls:
A new section, R1.2.6, requires Responsible Entities to formally incorporate security controls related to vendor electronic remote access into their BES Cyber Systems.
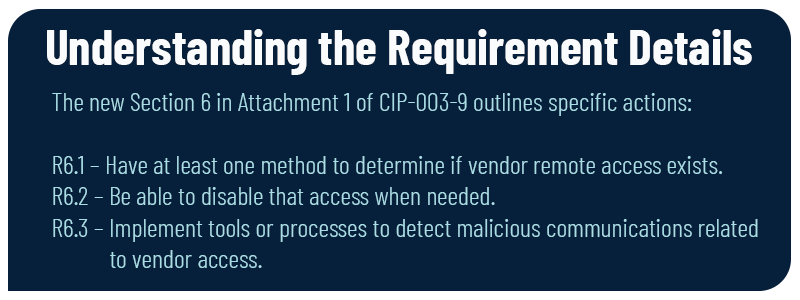
- Entities must be able to identify and disable vendor remote access:
Attachment 1, Section 6 mandates methods for identifying and disabling vendor electronic remote access connections.
- Entities must detect malicious vendor communications
Also in Attachment 1, Section 6, Responsible Entities must have a process for detecting known or suspected malicious inbound and outbound communication associated with vendor access.
These additions reflect an increased focus on managing third-party risks, particularly in environments that might otherwise be considered less critical due to their "Low-Impact" classification.
Where to Start: Steps for Compliance
1. Review and Update Your Cybersecurity Policies
Ensure your policies reflect the new requirement (R1.2.6). This includes updating your documentation for Low-Impact BES Cyber Systems to account for vendor remote access security controls. If needed, provide policy-specific training for staff.
2. Develop a Vendor Remote Access Plan
- Engage with vendors early to identify changes – especially if contract updates are needed or additional training is required
- Document your procedures for granting and revoking access
- Describe any electronic or procedural controls in place
- Clearly outline what tools you're using to detect malicious communications, such as intrusion detection systems or access monitoring tools
3. Establish Your Compliance Approach
- Create a plan to demonstrate compliance with the new requirements
- Identify your preventive, detective, and corrective controls
- Be prepared to show auditors your documentation and control evidence
Looking Ahead: What’s Next in the Standards Pipeline?
More changes are on the horizon with Project 2023-04, which focuses on further updates in CIP-003-10, following a review by the Low-Impact Criteria Review Team (LICRT). This initiative reflects concerns about coordinated cyber threats targeting Low-Impact BES Cyber Systems.
Even more significantly, a proposed update – CIP-003-11 – seeks to consolidate electronic access requirements by merging Sections 3 and 6 of CIP-003 Attachments 1 and 2. The Standards Committee approved this direction in March 2023.
To give organizations time to adapt, NERC has confirmed that entities will have at least three years from the effective date of CIP-003-9 to implement any new controls introduced in CIP-003-11. However, the earlier you address these changes, the better prepared you will be when the deadline arrives.
While Low-Impact assets may not carry the same weight as Medium or High-Impact systems, they still pose real cybersecurity risks – especially when remote vendor access is involved. The updates to CIP-003-9 reflect a growing awareness of that risk and a push for stronger, more consistent protections across the grid.
Now is the time to update your policies, engage your vendors, and evaluate your controls to stay ahead of compliance and build resilience into your systems. CIP compliance can be overwhelming – HSI advisors are experienced in Low-Impact CIP requirements and can help you develop processes, write procedures, create training, and ensure compliance.

6 Must-Do Steps for Low-Impact Entities: CIP-003-9 Compliance Checklist
With new requirements under CIP-003-9 now in effect, it’s important to take a structured approach to updating your policies, controls, and vendor relationships. Use this checklist to stay on track and simplify your path to compliance.
Your CIP-003-9 Compliance Checklist
✅ 1. Review and Update Cybersecurity Policies
Ensure your policies include vendor remote access controls (R1.2.6). Schedule training for teams if needed.
✅ 2. Identify Existing Vendor Remote Access
Document how you determine if vendor access exists (R6.1). Include both authorized and unauthorized pathways.
✅ 3. Define Methods to Disable Vendor Access
Establish clear procedures for disabling access quickly and securely (R6.2).
✅ 4. Deploy Tools to Detect Malicious Communications
Implement systems to detect suspicious vendor activity (R6.3), including both inbound and outbound threats.
✅ 5. Engage Vendors Early
Communicate upcoming changes. Clarify expectations, discuss potential contract updates, and determine whether vendor-specific training is needed.
✅ 6. Document Preventive, Detective, and Corrective Controls
Prepare to demonstrate how your organization identifies and manages risks tied to vendor remote access. Be audit-ready.
Looking Ahead:
Prepare for additional updates under CIP-003-10 and CIP-003-11. These standards will further refine access requirements and aim to consolidate guidance – so now is a good time to build a scalable, future-proof compliance program. HSI compliance advisors are ready to help you put your program in place.


